TCP Hijacking
The goal of the TCP session hijacker is to create a state where the client and server are unable to exchange data, so that he can forge acceptable packets for both ends, which mimic the real packets. Thus, he is able to gain control of the session. At this point, the reason why the client and server will drop packets sent between them is because the serv er’s sequence number no longer matches the client’s ACK number and likewise, the client’s sequence number no longer matches the server’s ACK number. In “Simple Active Attack Against TCP,” Laurent Joncheray refers to this state as the“desynchronized state” whereas the state where the TCP session is open and data is being exchanged is referred to as the “established state.” To achieve the creation of the desynchronized state, the hijacker can employ different techniques: IP Spoofing: Source Routed PacketsIP spoofing is “a technique used to gain unauthorized access to computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host.” The trusted host, in the case of session hijacking, is the client. In employing this technique, the session hijacker obtains the IP address of the client and modifies packet headers to indicate that they come from that IP address. This technique allows the hijacker to create his/her own acceptable packets to inject into the TCP Session. The packets are source-routed, meaning that the sender specifies the route the packet will take to get to the destination IP. Using these source-routed packets, the hijacker can route the packets to his host and fool the server into thinking it is communicating with the victim (the client). Once the hijacker has successfully spoofed an IP address, he determines the nex t sequence number that the server expects and uses it to inject the forged packet into the TCP session before the client can respond. By doing so, he creates the “desynchronized state.” The sequence and ACK numbers are no longer synchronized between client and server, because the server registers having received a new packet that the client never sent. Sending more of these packets will create an even greater discrepancy between the two hosts.
Blind Hijacking
If source routing is disabled, the session hijacker can also employ blind hijacking where he injects his malicious data into intercepted communications in the TCP session. It is called “blind” because the hijacker
can send the data or commands, but cannot see the response. The hijacker is basically guessing the responses of the clien t and server. An example of a malicious command a blind hijacker can inject is to set a password that can allow him access from another host.
Man in the Middle: Packet Sniffer
This technique involv es using a packet sniffer that intercepts the communication between the client and server. With all the data between the hosts flowing through the hijacker’s sniffer, he is free to modify the content of the packets. The trick to this technique is to get the packets to be routed through the hijacker’ s host. In “Theft On The Web: Prevent Session Hijacking,” Lam, LeBlanc, and Smith list two “tricks” that hijackers use to redirect traffic to create this “man in the middle” situation. The first technique is to use forged ICMP (Internet Control Message Protocol) packets to redirect traffic between client and server through the hijacker’s host. ICMP is an extension of IP that is used primarily to send error messages indicating problems processing packets through a connection. In this case, the hijacker is forging messages to fool the client and server into thinking that the route through his host is better than the original path (better as in faster, shorter, or non-error prone).The second technique is ARP spoofing. ARP stands for Address Resolution Protocol. ARP tables are used by each host to map local IP addresses to hardware addresses or MAC addresses. ARP spoofing involv es sending out forged ARP replies to fool the host broadcasting the ARP request into updating his ARP table, mapping the IP to be impersonated to the hijacker’s hardware address. All traffic intended for that IP will be delivered to his host instead. He can then choose to alter and forward the packets to the real host.
Tools
1)Hunt and
2)Juggernaut
3)TTyWatcher
4)IPWatcher
Practical tcp session hijacking
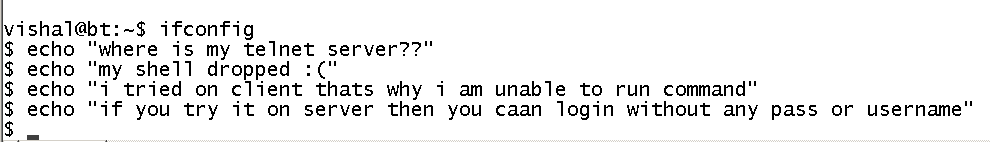 |
| Victim :Telnet CLient typing commands |
 |
| Now we are acting as telnet server and capturing all commands which client is typing
HaPpY S3ss1on Hij4Ck1ng!!!
|


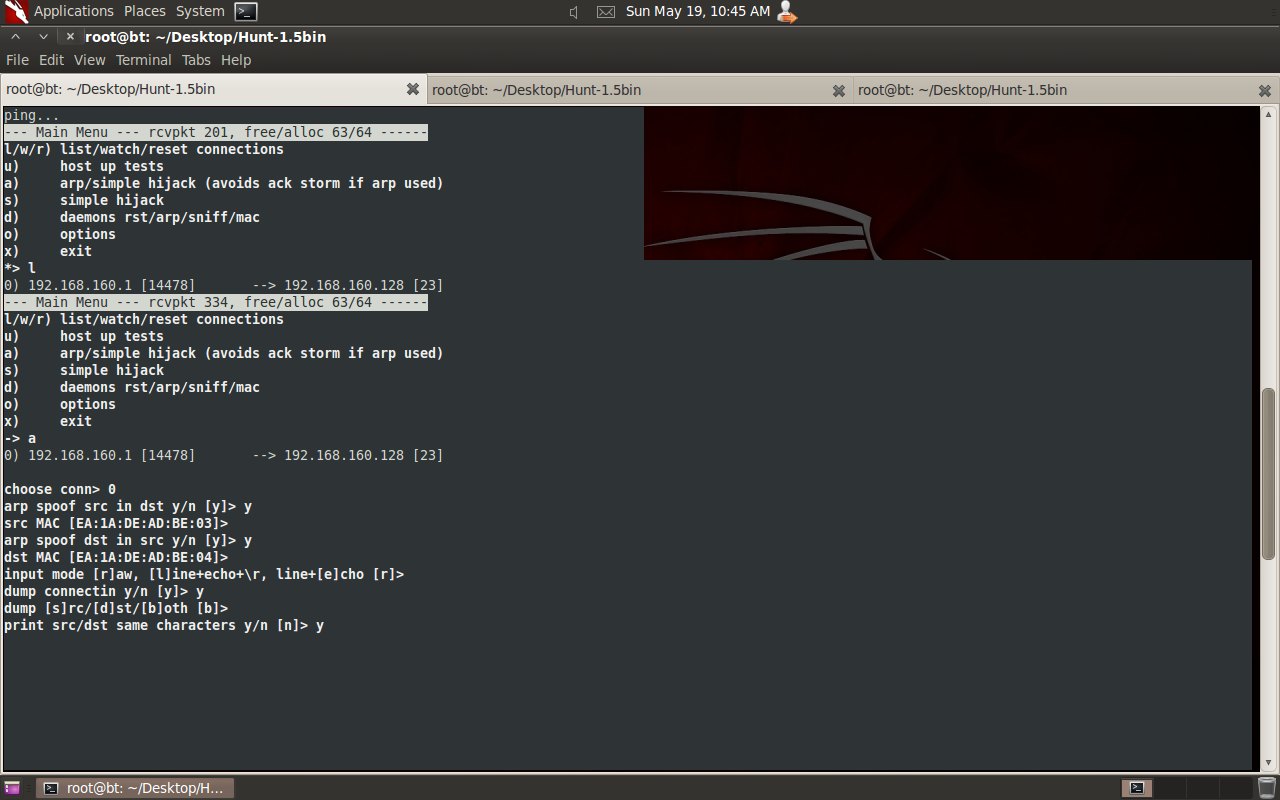

Comments
Post a Comment